Demystifying JAM - PBA6
Original Slide Contents:
Note:
- blog.kianenigma.com/posts/tech/demystifying-jam/presentation-pba
- https://blog.kianenigma.com/posts/tech/demystifying-jam/presentation/
- blog.kianenigma.com/posts/tech/demystifying-jam/
This Talk
- Understand what JAM is
- JAM's role in the broader Web3 vision
Understanding What JAM Is
aka. Demystifying JAM
Polkadot 1
- Social
- OpenGov
- DOT Token → Security
- Fellowship
- Technological
- Heterogeneous Execution Sharding, with Shared Security
Note:
Sharding enabled by the use of ELVES, and heterogeneity enabled by the use of WASM.
ELVES: Efficient Execution Auditing for Blockchains under Byzantine Assumptions
Heterogeneous Execution Sharding, with Shared Security
Let's break it down:
- Execution Sharding
- With Shared Security
- Heterogeneous
--
Sequential Blockchain
Note:
- Opposite of execution sharding
- How blockchains usually work
--
(Poorly) Execution Sharded
- Sharding the validator set: less security
--
Execution Sharded with Shared Security
- ELVES and Cynical Rollups
- Core Model
Note:
Original vision of ETH 2 was to be this, with 64 shards.
--
Heterogeneous
- WASM bytecode
--
Now You Get It?
Execution Sharding + With Shared Security + Heterogeneous
--
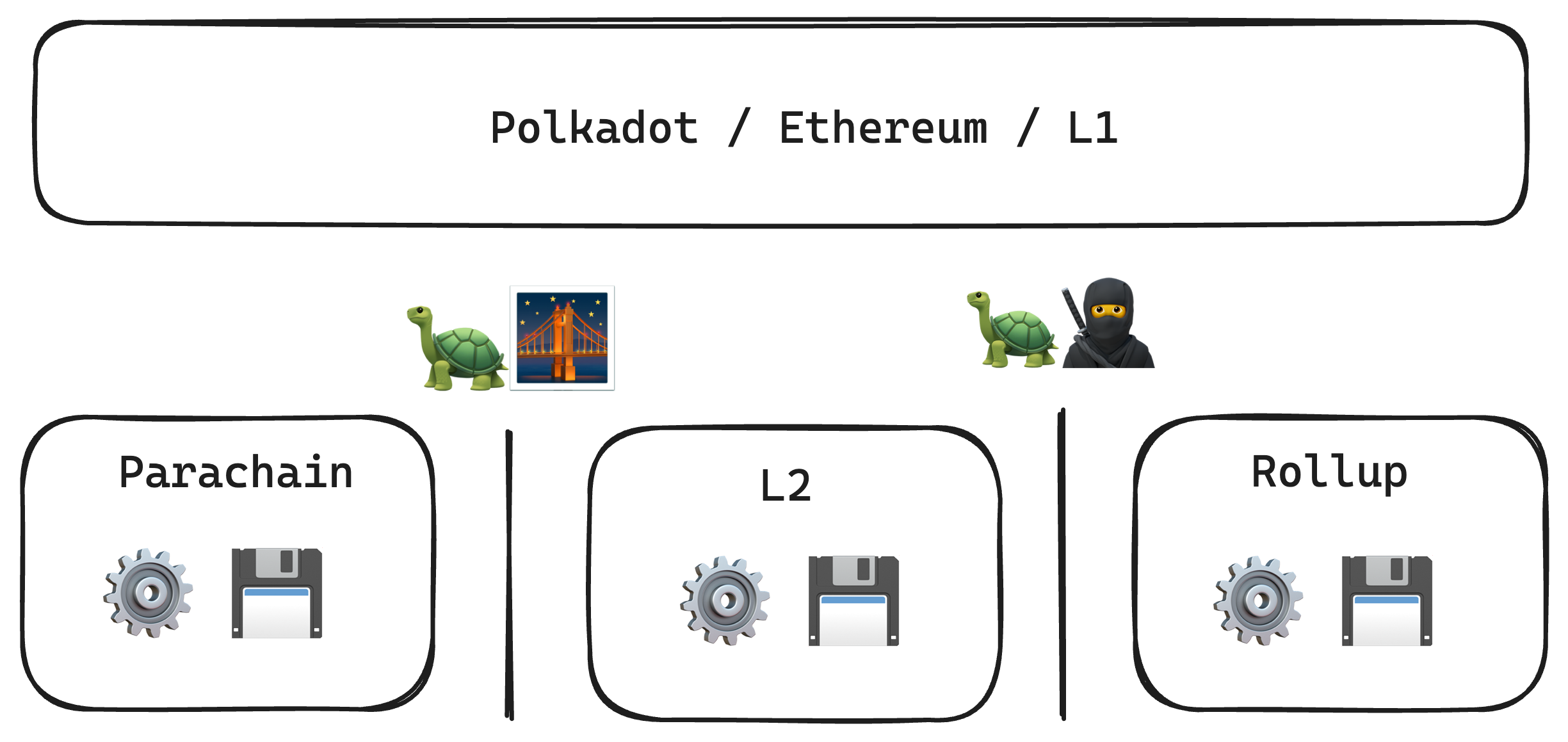
Evolution of Polkadot
... is all about flexible usage of cores
- You need more to get more out of your core? Async Backing!
- You need more cores? Elastic scaling!
- You don't want to commit to 6m? Agile-coretime!
- You need less than one core? On-demand coretime!
- You want to do something other than a parachain in your core? JAM!
Path of a Parachain Block
--
Path of a Parachain Block
--
Path of a Parachain Block
--
Path of a Parachain Block
Note:
In the existing Polkadot, the block itself is put into the DA for further auditing.
--
Path of a Parachain Block
Note:
- Execution by core validators + made available for further auditing
- State root updated by all Polkadot validators
--
Polkadot's Primitives
- In-core execution, with access to DA
- On-chain execution, with access to the main Polkadot state
--
Polkadot's Primitives
- Polkadot currently allows you to do a limited thing in-core, and on-chain. What are they?
- In-core: Re-execute the PVF, make the PoV accessible to DA
- On-chain: Small signature updates
--
Aside: Blockspace vs. Coretime
In-core, on-chain dualism is unique to execution sharding
Note:
This is why the word blockspace, despite being wildly adopted, is not very sensible in Polkadot, because we have various modes of blockpsace. This is why the word coretime is sometimes used instead of blockspace.
JAM
Now you know everything to understand JAM.
--
JAM (0)
Gutting of Polkadot such that the following are directly exposed to developers.
- What happens In-core
- What is placed in Data Availability from the core
- What happens On-chain
Note:
A parachain can only control what happens in-core. It cannot really control what happens on-chain. It also cannot readily add any data to the Data availability layer (well, it can, using remarks, which is a hack)
--
JAM (1)
- ..and removes a lot of parachain-centric opinions from Polkadot's core protocol.
--
JAM (2)
- ..and is therefore intended to be an evolution for the Polkadot Relay Chain.
- Parachains, Governance, Staking, AssetHub and everything else remains intact.
Removing Opinions
- JAM is programmable via a Service (PVM Bytecode)
- Invocation of a service are called a Work Item
- A group of work Items are called Work Package.
Note:
--
In-core and On-chain
- A Service is:
fn refine(): What happens in-corefn accumulate(): What happens on-chainfn on_transfer(): Send messages to other services post accumulate
--
Refine
- Massive amounts of gas available (5s PVM)
- Access to data availability
- 1.5 PB maximum size / 6s propagation time
- Can receive up to 12MB of input data (from DA, or extrinsic data)
- No direct access to the JAM state (stateless)
- Except preimages.
- Can Invoke child PVMs
--
Accumulate
- Direct access to the JAM state (stateful)
- Less gas available (10ms PVM)
- Fully synchronous: Access the refine results of all other services, from possibly all other cores at once.
--
JAM (Recap)
Allowing Services to program exactly how they want to use:
- In-core execution
- On-chain execution
- Data availability
Path of a JAM Work Package
--
Path of a JAM Work Package
Path of a JAM Work Package
Path of a JAM Work Package
--
Path of a JAM Work Package
--
Path of a JAM Work Package
JAM
PVM
- Metered (benchmarking 🤢)
- Very fast (45% native)
- PVM instance can invoke another instance
- Service can invoke a parachain, or smart contract, or anything else
- Easy to pause and resume -> Continuation
JAM Misc
- JAM offers a similar bulk coretime purchase model to that of Polkadot
- No per-transaction purchase
- Much greater economic freedom for services/applications!
--
JAM Misc (1)
- JAM offers a much more flexible
Authorizationmechanism for core utilizationauthorize() -> refine() -> accumulate() -> on_transfer()
JAM Envisioned Services
CoreChainsCoreVM/CoreBoot/JAMDockerCorePlay
--
CoreChains
- Entire Polkadot 2 + Parachains is one service
Note: This is an example of JAM's low abstraction level
--
CoreVM
- Running normal applications on JAM
- Demonstration of PVM's "continuation"
- Utilizes DA to store intermediate program state, such as the stack and registers
- 🎯 DOOM!
--
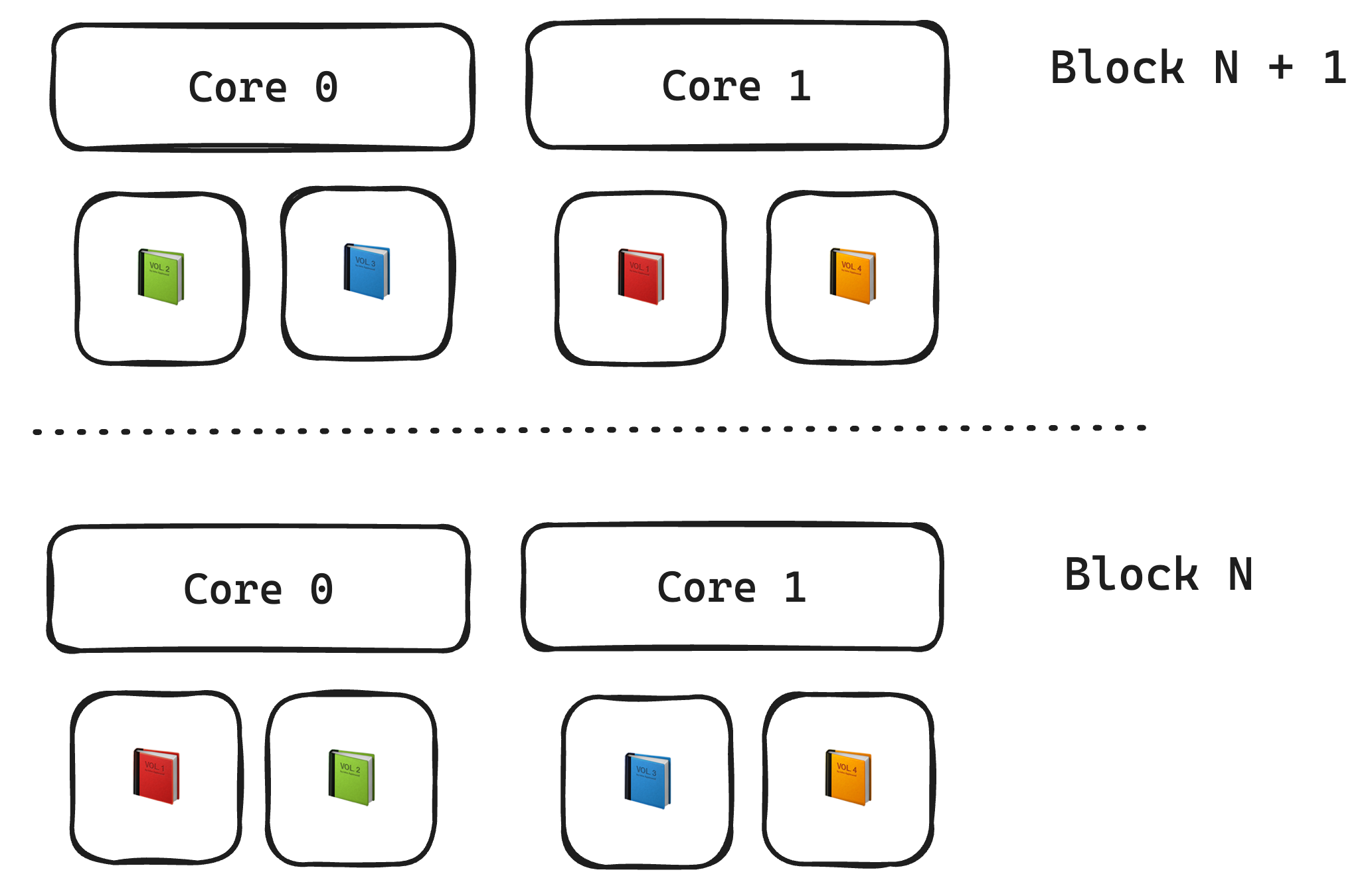
CorePlay
- Ultimate actor based smart contract platform
- Non-persistent state partitioning
Note: This is a prime example of JAM's transient decoherence in action
--
CorePlay
JAM Introduction Ends
Questions?
The Web3 Vision and JAM
- Abstract look at blockchain/Web3 technology
Blockchain Mental Models
- 🤮 Database
- ♾️ State Machine
- 💻Computer
--
Blockchain Mental Models
- A computer has two main primitives
- ⚙️ Computation
- 💿 Storage
--
Generic Blockchain Computer
- A blockchain/Web3 computer has:
- ⚙️ + 👮♂️ Secure computation
- Canonical ordering + auditability of the said secure computation
- Secure, public-by-default storage
--
- ⚙️ + 👮♂️ Secure computation
Sequential, Non-Sharded Blockchain Computer
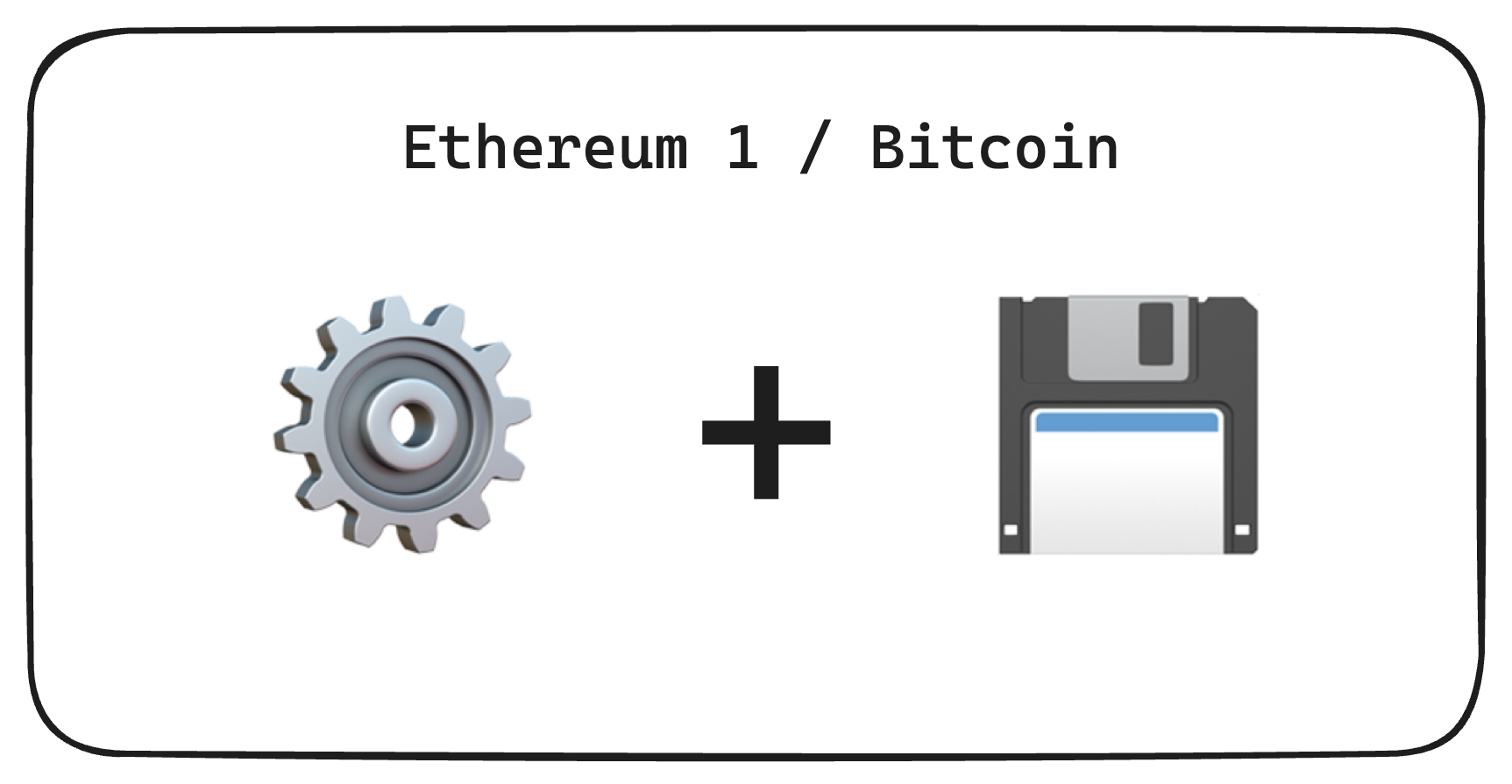
- Limited + Expensive computation
- Limited + Expensive storage
- Fully coherent environment, albeit kinda useless
--
Sharded Blockchain Computer
- Abundant computation
- Abundant storage
- Limited + Expensive coherent L1 storage
- Abundant incoherent rollup storage
- Fully incoherent environment, which still makes it kinda useless
- Multi-core CPU, without any shared memory!
Note:
This model is potentially useful, if you want a lot of throughput, high customization, and don't care much about interoperability
--
JAM: Supercomputer
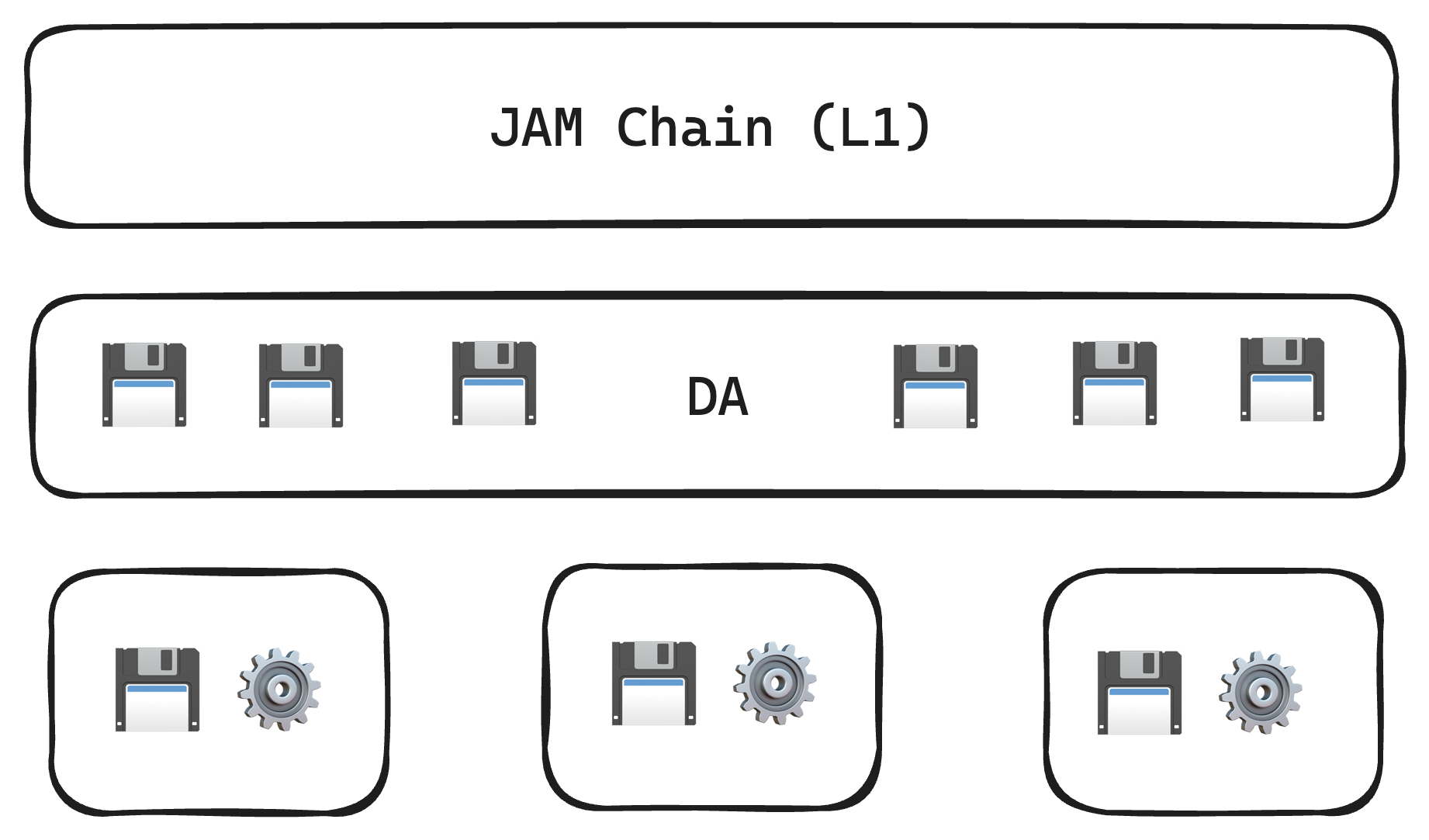
- Multi-core CPU with shared memory!
- JAM is a supercomputer. It is most performant Web3 computer one can build, without sacrificing security
--
JAM: Supercomputer
- Abundant secure computation (ELVES)
- Abundant storage
- Limited coherent L1 storage (JAM State)
- Abundant, mostly coherent DA storage (
) - Fully incoherent service storage
--
JAM: Web3 Cloud
- JAM is like supercomputer that takes the has the most high quality primitives of the Web3 computer, and exposes them all to developers
- JAM is the (virtual) Web3 hardware on top of which we can build what we may dare call Web3 Cloud.
Questions
Appendix / Backup Slides
--
Kernel Update Analogy
Note:
Hardware is what provides compute and bandwidth, and the kernel is part of the OS that moderates the hardware access.
Current Polkadot. A lot of stuff is part of the "Kernel/OS".
--
--
--
Work Item
graph LR subgraph WorkPackage WI1[Work Item 1] WI2[Work Item 2] WI3[Work Item 3] end subgraph WorkReport WR1[Work Result 1] WR2[Work Result 2] WR3[Work Result 3] end WI1 --> WR1 WI2 --> WR2 WI3 --> WR3
-
Comments
- Made with Obsidian-Digital-Garden
- © Kian Paimani . Content on this site is licensed under a Creative Commons Attribution 4.0 License.